8. Security
- -
Motivation
- Field of network security
- how bad agents can attack computer networks
- how we can defend networks against attacks
- how to design architectures that are immune to attacks
- Internet not originally designed with (much) security in mind
- original vision : “a group of mutually
trustingusers attached to a transparent network
- Internet protocol designers playing “catch-up”
- security considerations in all layers
→ OSI의 각 layer에서 security와 관련된 issue를 다뤄야한다는 것
- original vision : “a group of mutually
Bad Agent Example
Packet Interception
Packet sniffing
- broadcast media (shared Ethernet, wireless)
promiscuous network interfacereads/records all packets (e.g. including passwords) passing by

Denial of service (DoS)
Attackers make resources (server, bandwidth) unavailable to legitimate traffic by overwhelming resource with bogus(illegal) traffic

- Select target
- Break into hosts around the network
- Send packets to target from compromised hosts
Fake Identity : IP spoofing
Send packet with false source address

Lines of Defense
- Confidentiality via encryption : 암호화를 통해서 정보의 기밀성을 보장하는 것. 즉, 허가되지 않은 사람들이 해당 내용을 읽거나 해독할 수 없게끔하는 것
- Authentication : 본인 확인 절차이다. 예를 들어 휴대폰의 SIM 카드는 사용자가 네트워크에 인증하도록 돕는 역할을 수행한다.
- Integrity checks : digital signature를 통해 데이터가 변경되거나 조작되는 것을 방지하거나 탐지하게 된다.
- Access restrictions : 비밀번호로 접근을 제한시키거나
Virtual Private Network(VPN)의 사용등으로 접근을 제한하는 것이다. 즉 미인증된 사용자가 민감한 resource에 접근하는 것을 막는다.
- Firewalls : 네트워크의 접근 및 핵심 부분에 위치한 specialized된 device이다.
→ 기본적으로 모든 것을 차단하고 필터링 규칙에 따라 특정 패킷만을 통과시킨다. 이에 따라 DoS 공격과 같은 보안 위협을 감지하고 대응할 수 있게 된다.
Goals of Network Security
- Confidentiality : 수신자와 의도된 receiver가 해당 message의 내용을 이해할 수 있어야 한다.
- sender encrypts message
- receiver decrypts message
- Authentication : sender, receiver want to confirm identity of each other
- Message integrity : sender, receiver want to
ensuremessage not altered without detection
- Access and availability : services must be accessible and available to users
→ AoS같은 상황이 일어나면 안된다는 것이다.
Principles of Cryptography : Symmetric Key
The Language of Cryptography

Breaking an Encryption Scheme
We can distinguish three different scenarios, depending on what information the intruder has
Cipher-text only attack
Trudy want to analyze the cipher-text so that he want to find the original message or public key
→ With no certain information about the contents of the plain text message
There is two approach
- brute force : search through all keys
- statistical analysis
Known-plaintext attack
In this case, the intruder know for sure that some words appeared in the cipher-text message. By using that information, the intruder can determined the (plaintext, cipher-text) pairings for some letters.
Chosen-plaintext attack
In this approach, trudy can get cipher-text for chosen plaintext
→ 원하는 plaintext를 선택하고 그 정보로부터 사용된 암호화 키나 알고리즘을 찾아내려고 하는 것이다.
Symmetric Key Cryptography
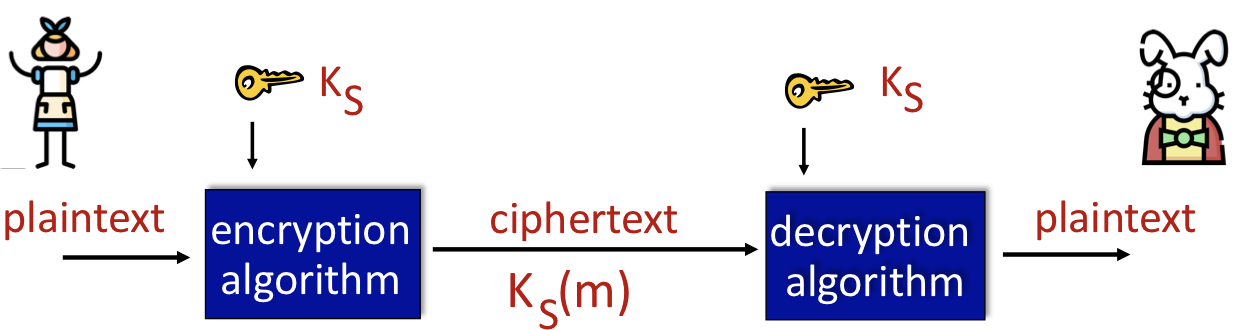
Sender와 Receiver가 동일한 key KS를 사용하는 것이다.
예를 들어 다음과 같은 상황을 생각하면 된다.
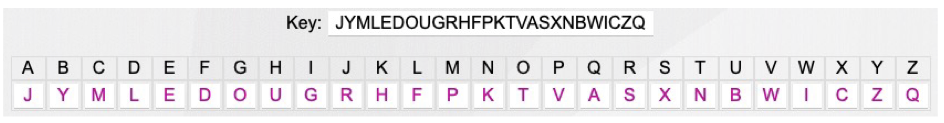
하지만 이와 같은 방식은 statistical analysis 공격에 취약할 수 밖에 없다.
- e, t는 일반적인 영어에서 통계적으로 가장 빈번하게 사용된다는 점을 이용할 수 있다.
- 추가적으로 in, it, the, ion, ing 같은 단어들이 자주 사용된다는 점 또한 이용할 수 있다.
→ 이러한 취약점을 바탕으로 이러한 암호화방식을 쉽게 깰 수 있다.
Q : How do Bob and Alice agree on key value?
- 보안된 online channel
- Public Key Cryptography : 각자의 비밀키와 공개키 쌍을 생성하고, 서로의 공개키로 메세지를 암호화하여 전송한다.
Simple Encryption Scheme
- Substitution cipher : substituting one thing for another
A Better Encryption Approach
- n substitution ciphers : M1,M2,…,Mn
- cycling pattern
→ ex : M1,M3,M4,M3,M2
- for each new plaintext symbol, use subsequent substitution pattern in cyclic pattern
→ ex : dog : d from M1, o from M3, g from M4

Symmetric Key Crypto : DES

DES : Data Encryption Standard
- US encryption standard
56bit symmetric key, 64bit plaintext input
- Block cipher with cipher block chaining : 이전 블록의 암호문이 다음 블록의 암호화에 영향을 주는 것이다.
- How secure is DES?
- 56bit key encrypted phrase decrypted in less than a day by using brute force
- Making DES more secure
→
3DES: encrypt3times with 3 different keys
Symmetric Key Crypto : AES

AES : Advanced Encryption Standard
- Symmetric-key NIST standard, replaced DES
- Processes data in
128bit blocks
- 128, 192 or 256 bit keys
- Brute force decryption taking 1 sec on DES, takes 149 trillion years for AES
→ 그만큼 DES보다 AES가 더 안전한 암호화 방식이라는 것이다.
Principles of Cryptography : Public Key

- Sender, receiver do
noshare secret key
publicencryption key known toall
privatedecryption key known only to receiver
Requirements
- need KB+ and KB− such thatKB−(KB+(m))=m
- given public key KB+, it should be
impossibleto compute private key KB−
→ 이를 만족하는 algorithm이 RSA 이다.
Prerequisite : modular arithmetic
- x mod n : remainder of x when divide by n
- Facts
- {(a mod n)+(b mod n)} mod n=(a+b) mod n
- {(a mod n)−(b mod n)} mod n=(a−b) mod n
- {(a mod n)∗(b mod n)} mod n=(a∗b) mod n
- ay mod n=ay mod n mod n
Therefore,
(a mod n)d mod n=ad mod n
- Euler’s Theoremaϕ(n)=1(mod n)
if GCD of a and ϕ(n) is 1
💡이때, ϕ(n)은 Euler phi function으로 n보다 작거나 같은 양의 정수 중 n과 서로소인 것들의 개수이다. 만약 n이 n=pq (p,q is prime)이면 ϕ(n)=(p−1)(q−1)이다.Proof
ϕ is multiplicative. Therefore,
ϕ(ab)=ϕ(a)ϕ(b)In addition, if a is a prime
ϕ(a)=a−1Therefore, if n=pq where p,q are prime
ϕ(n)=(p−1)(q−1)
Public Key Encryption : RSA
It uses 2 big prime numbers to generate public key and private key.
→ Since, it requires exponential calculation, it is computationally more intensive than DES
Therefore, in reality, we use public key crypto like RSA to establish secure connection, then establish second key (symmetric session key) for encrypting data
Session key: KS- Bob and Alice use RSA to exchange a symmetric session key KS
- once both have KS, they use symmetric key cryptography
session key 는 한 세션 동안만 사용되는 임시적인 암호화 키이다.Note
- message : just a bit pattern
- bit pattern can be
uniquelyrepresented by an integer number→ thus, encrypting a message is equivalent to encrypting a number
💡예를 들어 10010001이라는 메세지가 있다고 했을 때 10진수로는 145로 유일하게 표현된다. 결과적으로 message를 encrypt한다는 것은 숫자를 encrypt한다는 것과 같은 말이다.
Creating public/private key pair
- Choose two large prime numbers p,q
- Compute n=pq, z=ϕ(n)
- Choose e (with e<n) that as
nocommon factors with z→ By Euler’s theorem ez=1(mod n)
- Choose d such that ed−1 is exactly divisible by z
→ ed mod z=1
Public key : (n,e)Private key : (n,d)💡e와 z가 서로소인 경우에는 해당하는 d가 unique하다. 이러한 d는 Extended Euclidean Algorithm을 통해 찾을 수 있다.
Encryption, decryption
- given (n,e) and (n,d) as computed above
- to encrypt message m, computec=me mod n💡단순히 e승 해주고 n으로 modular 연산을 취해주면 된다.
- to decrypt received bit pattern c, computem=cdmod n💡단순히 d승 해주고 n으로 modular 연산을 취해주면 된다.
It works since
Example

Another Important property
Security of RSA
Suppose you know the public key (n,e). How hard is it to determine d?
→ Essentially need to find factors of n without knowing the two factors p and q
- When p and q are known
- Find the value of Euler’s phi function : (p−1)∗(q−1)
- Find d by following equation by using
Extended Euclidean Algorithmed mod z=ed mod ϕ(n)=1
💡ϕ(n)을 계산할 수 있으므로 d를 쉽게 구할 수 있다.
- When p and q are unknown
- Factorize n
- Find the value of Euler’s phi function : (p−1)∗(q−1)
- Find d by following equation by using
Extended Euclidean Algorithmed mod z=ed mod ϕ(n)=1
💡이때 1번 과정이 굉장히 어렵기 때문에 RSA Algorithm이 안전하다는 것이다. e와 z가 소인수이기만 하면 d의 유일성은 보장이 되고 고정된 e에 대해서 소인수인 z는 무한 개이므로 d 또한 z를 모르면 개수가 무한개이다.
Message Authentication and Integrity
Goal : Bob wants Alice to “prove” her identity to him
Protocol 1.0

But it has a problem

Protocol 2.0
Alice says “I am Alice” in an IP packet containing her source IP address

Protocol 3.0
Alice says “I am Alice” and sends her secret password to “prove” it
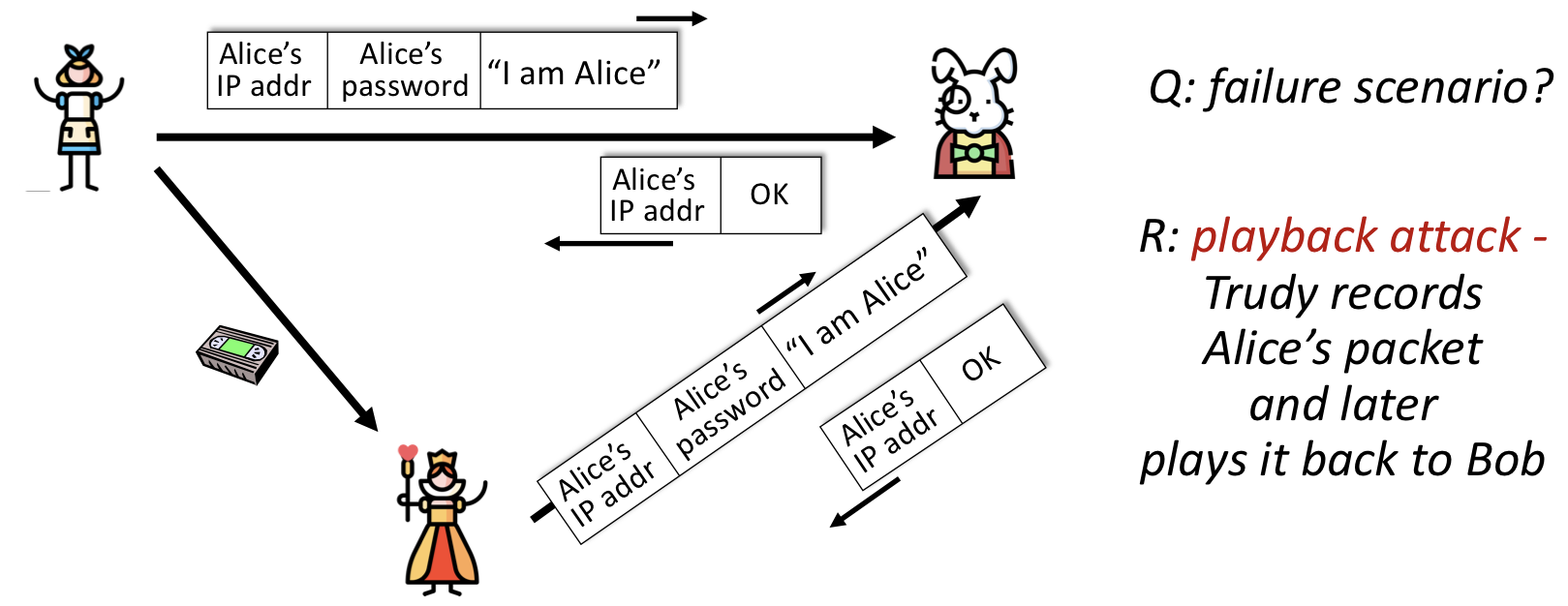
Protocol 4.0
Goal : avoid playback attack
nonce : number (R) used only once in a life time
To prove Alive is “live”, Bob sends Alice nonce, R
→ Alice must return R, encrypted with shared secret key
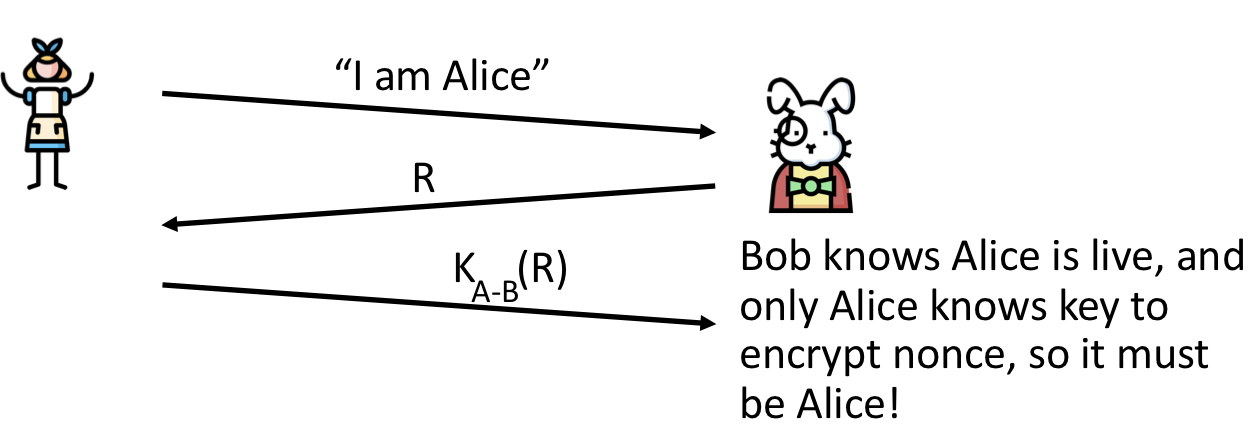
→ 즉 nonce R을 Alice에게 보내고, Alice는 공유된 비밀 키로 암호화된 R을 반환함으로써 Authentication을 한다는 것이다.
shared symmetric key 라는 것이다.Protocol 5.0
앞서 언급한 것처럼 Protocol은 shared symmetric key를 사용한다. Protocol 5.0에서는 public key technique를 사용해서 보다 좀 더 안전하게 Authentication을 진행하려고 한다.
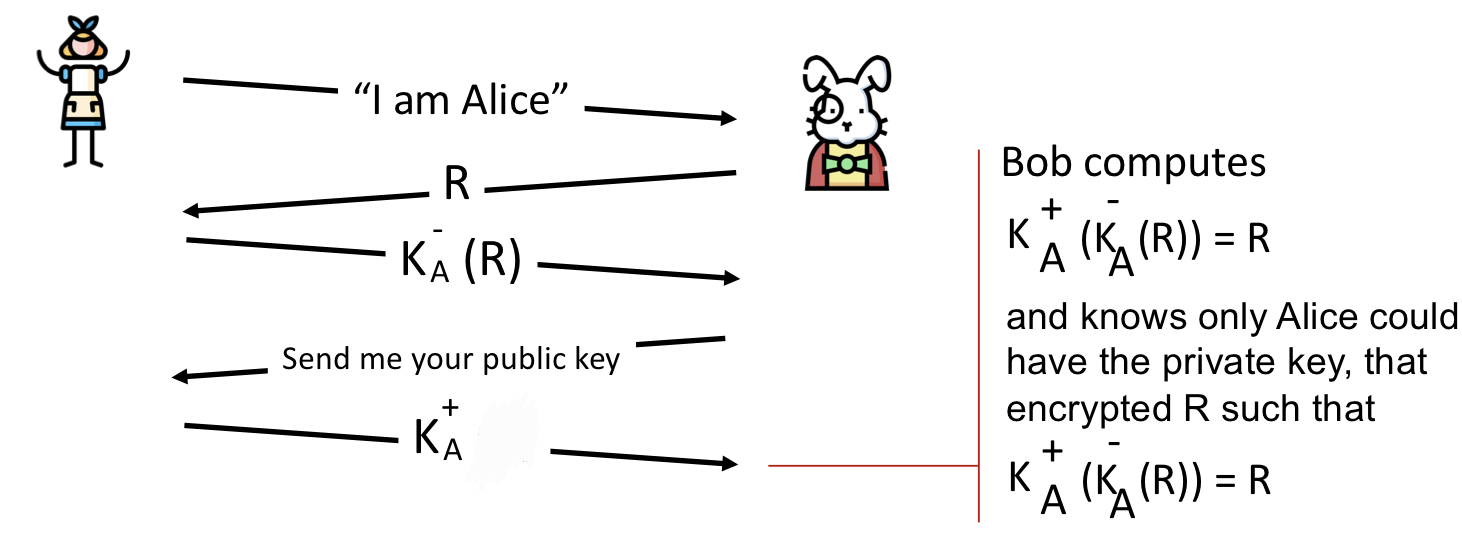
But, it is not enough

But, there’s still a flaw in Protocol 5.0. It is called middle attack
→ Intruder poses as Alice to Bob. On the other hand, that intruder poses as Bob to Alice.
Digital Signatures
Cryptographic technique analogous to hand-written signatures:
sender digitally signs document : he is document owner/creator

- verifiable, non-forgetable
→ recipient can prove to someone else that
onlycreater must have signed that document
- simple digital signature for message m
- Bob signs m by encrypting with his private key KB−
- The encrypted message is represented by KB−(m)
Procedure
- Suppose Alice receives message m, with signature : KB−(m)
- Alice verifies m signed by Bob by applying Bob’s public key KB+ to KB−(m) then checks KB+(KB−(m))=m
- If KB+(KB−(m))=m, whoever signed m must have used Bob’s private key
Alice thus verifies that
- Bob signed m
- no one else signed m
- Bob signed m and not m′
non-repudiation : Alice can take m, and signature KB−(m) to court and prove that Bob signed m
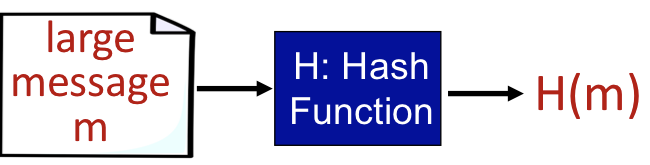
Message Digests
However, it is computationally expensive to public-key-encrypt long messages
Goal : fixed length, easy to compute digital fingerprint
→ Use Hash function!

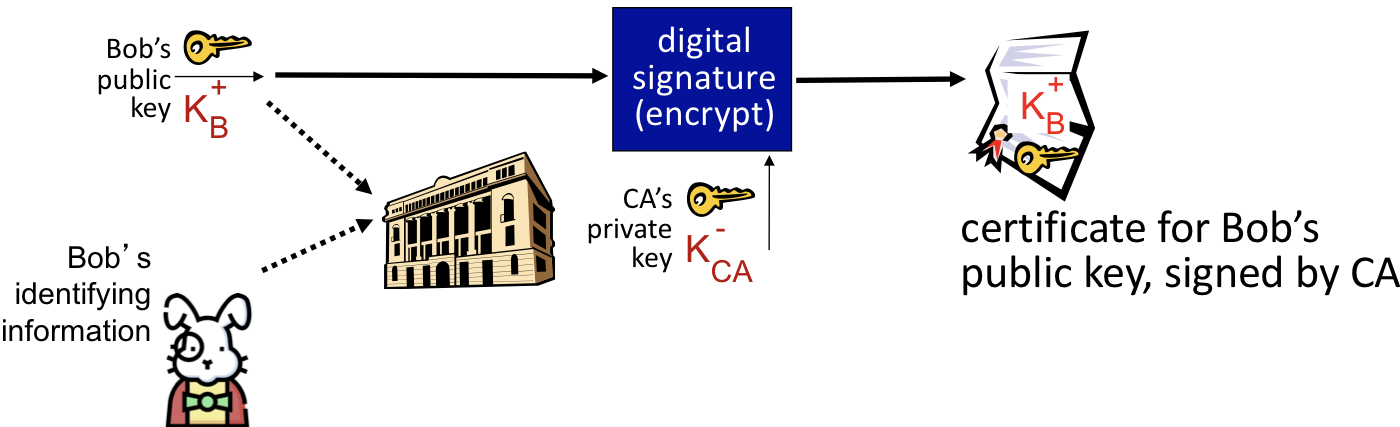
Public Key Certification Authorities
- Certification authority (CA) : Certification authority links the public key to a specific entity, E
- Entity : An entity, such as an individual website or router, registers its public key with the CA. At this point, it must provide
proof of identityto the CA
- The CA then creates a certificate that binds the identity E to E’s public key
- This created certificate includes E’s public key and is digitally signed by the CA - essentially stating “this is E’s public key”
When Alice wants Bob’s public key:
- Gets Bob’s certificate
- Apply CA’s public key to Bob’s certificate, get Bob’s public key

Security Across TCP/IP Layers
Transport-layer Security (TLS)
- Widely deployed security protocol above the transport layer
→ Supported by almost all browsers, web servers :
https(port 443)
- Provides
- confidentiality : via
symmetric encryption
- integrity : via
cryptographic hashing→ sender가 보낼 message에 대한 hash 값을 생성하고, 해당 hash 값은 메세지와 함께 수신자에게 전송된다. 수신자 측에서는 받은 메세지로부터 동일한 hash function을 사용해서 새로운 hash 값을 생성한 뒤 이를 비교한다. 이를 통해 중간에 메세지가 변경되거나 손상되었는지 여부를 판단할 수 있다.
- authentication : via
public key cryptography
- confidentiality : via
- What is needed
handshake: Alice, Bob use their certificates, private keys to authenticate each other, and createsession key💡일반적으로 server는 client에게 자신의 certificate를 보낸다. client가 해당 certificate를 보내면 CA의 public key를 활용하여 digital signature를 복호화하고 해당 값과 원본 인증서의 hash 값을 비교함으로써 유효성을 검사한다.💡실제로 public, private key는 매우 큰 2개의 소수의 곱을 사용하기 때문에 computational cost가 크다. 그래서 안전하게 handshaking을 진행한 이후에는session key를 이용해서 데이터를 주고받게 된다.How to create a session key?
- premaster secret 생성: 클라이언트는 랜덤한 값을 premaster secret으로 선택한다.
- premaster secret 전송: 클라이언트는 이 premaster secret을 서버의 공개키로 암호화하여 서버에게 전송한다.
- master secret 생성: 서버는 자신의 개인 키로 premaster secret을 복호화하고, 클라이언트도 동일한 master secret을 가지고 있다. 그런 다음, 둘은 이 값을 기반으로 마스터 시크릿을 계산한다.
- session key 생성: 마지막으로, 클라이언트와 서버 모두 master secret, Client Hello 메시지의 랜덤 값, Server Hello 메시지의 랜덤 값을 사용하여 session key를 독자적으로 계산한다.
key derivation: Alice, Bob use shared secret to derive set of keys💡해당 key들은 데이터 전송에 사용되며, symmetric encryption에 사용된다.
- data transfer
- connection closure : special messages to securely close connection

- TLS provides an
APIthat any application can use
IP Sec Protocol
- Provides datagram level encryption, authentication, integrity for both user traffic and control traffic
- Two modes
- Two IPsec Protocols
- Authentication Header (
AH) protocol→ provides source authentication & data integrity but
notconfidentiality
- Encapsulation Security Protocol (
ESP) protocol→ provides source authentication, data integrity, and confidentiality
💡More widely used than AH
- Authentication Header (
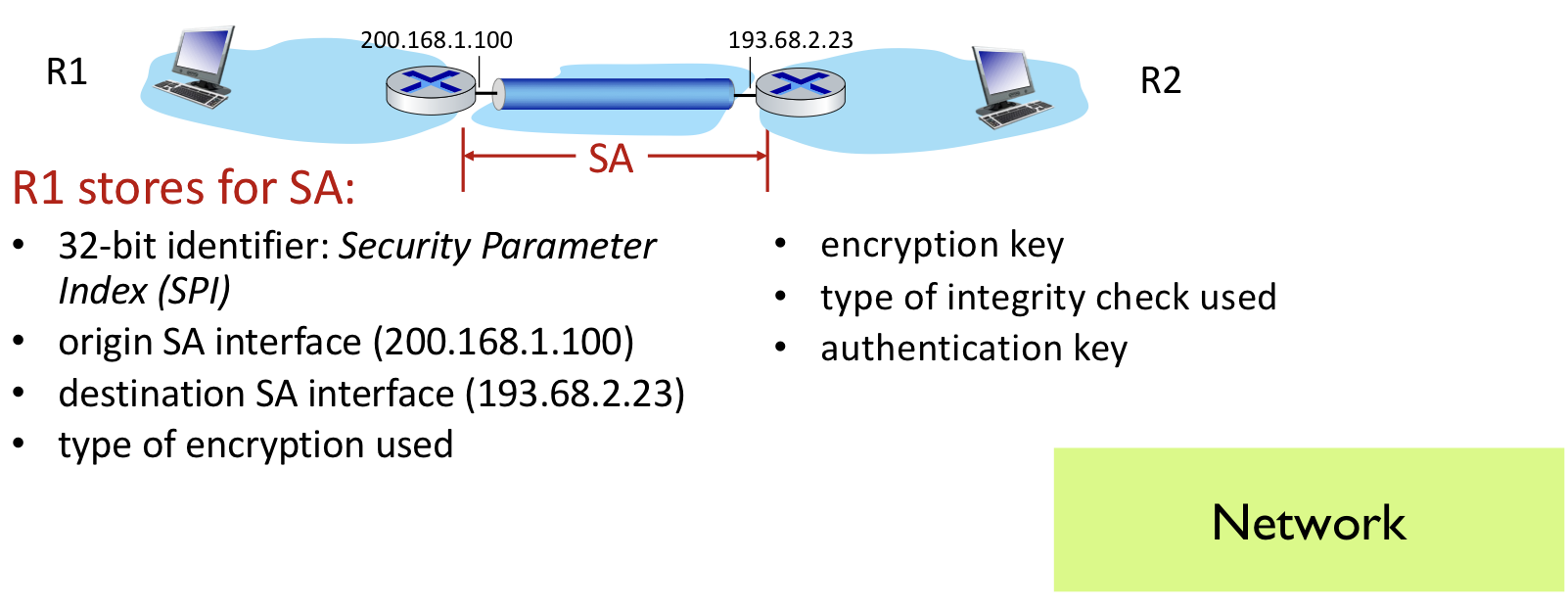
Security Associations (SAs)
IPsec protocol은 network layer에서 security를 제공하기 위해서 데이터를 전송하기 위해 Security Association을 설정하는 것을 포함한다. 이때 security association는 single directional하므로 양방향 통신을 위해서는 2개의 security association이 필요하다.
- Before sending data,
security associationestablished from sending to receiving entity
- ending, receiving entities maintain
state informationabout SA
Internet Key Exchange (IKE)
Internet Key Exchange는 IPsec 연결을 설정할 때 사용되는 protocol이다. 해당 protocol의 목적은 Security Association을 동적으로 형성하는 것이다.
→ 수작업으로 Security Association과 관련된 모든 정보들을 입력하는 것은 VPN 과 같이 endpoint들이 많은 환경에서는 적절하기 않다.
따라서 이러한 환경에서는 IKE가 사용된다.
IEEE 802.11 : Authentication, Encryption

For a mobile device to connect to an Access Point, it must go through the following steps
- Association : The mobile device establishes a connection with the AP over a wireless link
- Authentication : The mobile device must authenticate to the network via an Authentication Server (AS)
In this process, the Wi-Fi protected Access (WPA) protocol plays a key role. WPA provides a four-way handshake protocol for mutual authentication and derivation of shared symmetric session keys
→ WPA3 is the current version (2018)
Extensible Authentication Protocol (EAP) defines end to end request/response protocol between mobile device and AS
- RADIUS protocol for transmission over UDP/IP to the authentication server
- DIAMETER protocol is projected to eventually replace RADIUS
소중한 공감 감사합니다


